What is identity theft?
Whenever anyone utilises personal identification information to obtain additional monetary advantages or commit fraud, this is known as identity theft.
Personal identifying information may include the following:
- Full name
- Email address
- The address of a person's residence
- Social security number
- Logins and passwords for the internet
- The number of the bank
- Passport number
- Driver's license number
Thieves may use this information to perpetrate identity theft or sell it on the dark web once they gain access to it.
Summary
- When someone obtains your personal information and credentials to commit fraud, this is known as identity theft.
- Identity thieves are increasingly using computer devices to steal other people's data to commit identity fraud.
- Identity theft protection is a booming sector that monitors people's Social Security numbers, bank transactions, and credit reports.
Frequently Asked Questions (FAQs)
How does identity theft occur in the modern era?
The following are the most typical methods used by identity thieves to obtain a person's personal information:
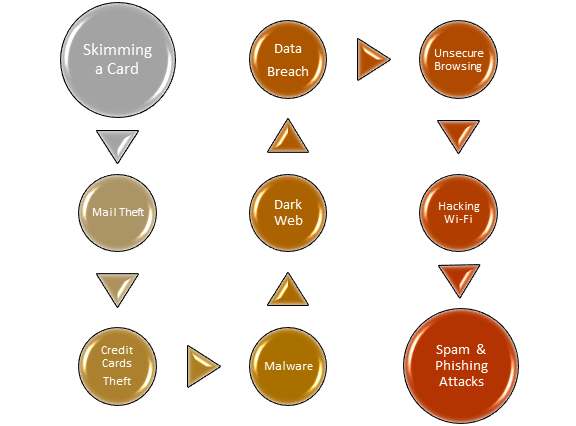
Breach of Data
When someone acquires unauthorised access to an organisation's data, this is known as a data breach. Full names, credit card numbers, and social security numbers are the most typical types of information taken in data breaches.
It is difficult to keep data safe from a data breach because people have multiple accounts to operate with numerous businesses and other organisations. Still, some actions may be taken to reduce the risk.
Unsecure Browsing
For the most part, anyone may surf the web safely, mainly if they stick to well-known websites. However, if any information is provided on an insecure site or a website that has been hacked, you risk putting vital information in the hands of a thief.
You may see an alert while visiting a potentially dangerous website, depending on the browser.

Source: © Flynt | Megapixl.com
Hacking Wi-Fi
Hackers could spy on a network if someone uses their phone or computer on a public network—coffee shop, airport, or department store Wi-Fi.
This means that whether you type in a password, social security number, credit card number, bank account information, or anything else, an intruder might easily intercept it and utilise it for their gain.
Theft of Mail
Identity fraudsters have been searching the mail for documents containing personally identifiable information.
You should remove any old mail which may contain personal information before discarding it.
Theft of Mobile Phones
Smartphones are a gold mine of information for identity thieves in the modern era, especially if your apps allow you to log in automatically without using a fingerprint or a password. So, if someone steals and unlocks your phone, they may be able to see the data stored in your apps, as well as your text messages, notes, emails, and other documents.
Check that your phone has a strong password, that passwords are not saved in plain text anywhere on the phone, and that biometric screening is correctly configured.
Spam and Phishing Attacks
Text messaging, email, and other kinds of electronic contact is used by some scammers to obtain your private information. The message typically appears to be from a credible source and requests that victims provide one or more data items.
For instance, a fake email claiming to be from your bank can include a link to a fake website that seems identical to the one it is duplicating. The website may then ask for a password and username, as well as your social security number and credit card details. Something odd may be an attempt at identity theft.
Theft of Credit Cards
One of the most basic types of identity fraud is credit card theft. If a thief finds access to your credit card, they can use it to make fraudulent purchases.
Credit card theft is most committed through data breaches, online retail accounts where card data is stored, credit card skimmers, and physical theft.
Source: Kalkine Media
Activity of Malware
Malware is a malicious program software that is meant to cause mayhem. For example, fraudsters may employ malware to monitor computer activities without knowing and stealing information.
Dark Web
Your personally identifiable information winds up on the dark web once it has been stolen. Unfortunately, it is not always the case that hackers steal information for personal gain; instead, they choose to sell it to others with possibly harmful motives.
The dark web, often known as the internet's curse, is a hidden network of websites that are not accessible through standard browsers. People who utilise a specific software hide their identity and activities on the dark web, making it a paradise for fraudsters. Anyone could buy your data if it winds up on a dark web marketplace, putting your identity in jeopardy.
Skimming a Card
Some fraudsters employ a skimming device that can be installed over a card reader on an ATM or a fuel pump and does not appear out of place. When someone uses a hacked machine to swipe a credit or debit card, the skimmer gathers the data from the card's magnetic stripe and either saves or sends it. This data can subsequently be used by a criminal to make transactions.
How do you combat identity theft?

Source: © Rjmiz | Megapixl.com
Here are some strategies for preventing identity theft:
- Keep your credit and debit cards and your Social Security and Medicare cards at home and only carry what you need in your wallet.
- Use only secure websites. "HTTPS" will be at the beginning of the URL (the "s" stands for "secure").
- Make each gadget and account's passwords hard and one-of-a-kind. A strong password consists of at least a dozen symbols, digits, and letters, or another option for creating a long passphrase that is difficult for a thief to guess yet easy for you to remember.
- Create notifications for your credit cards and bank accounts. Your bank, for example, may send you messages whenever you make a withdrawal from your checking account.
- Never give out personal information over the phone, especially if you did not initiate the call.
- If you suspect your account has been hacked, change your password right away.
- On all accounts that support it, enable two-factor authentication.
- Receipts, bills, mail, and other documentation containing sensitive information should be destroyed before being thrown away.
- Responding to emails, clicking links, or opening attachments from unknown or untrustworthy sources may include malware.
- Keep track of your financial accounts and credit reports to watch for changes you did not make.
 Please wait processing your request...
Please wait processing your request...